Short Biography
I completed both my bachelor and master degrees in Media Informatics at the LMU Munich. In 2021, I started my PhD with Prof. Florian Alt at the University of the Bundeswehr Munich as part of the dtec.bw project MuQuaNet. Since 2025, I am also a member of the Media Informatics Group at the LMU Munich.
My research focuses on tangible privacy and security interfaces, but I am also interested in the IoT, behavioral biometrics, accessibility and fabrication.
Research Highlights
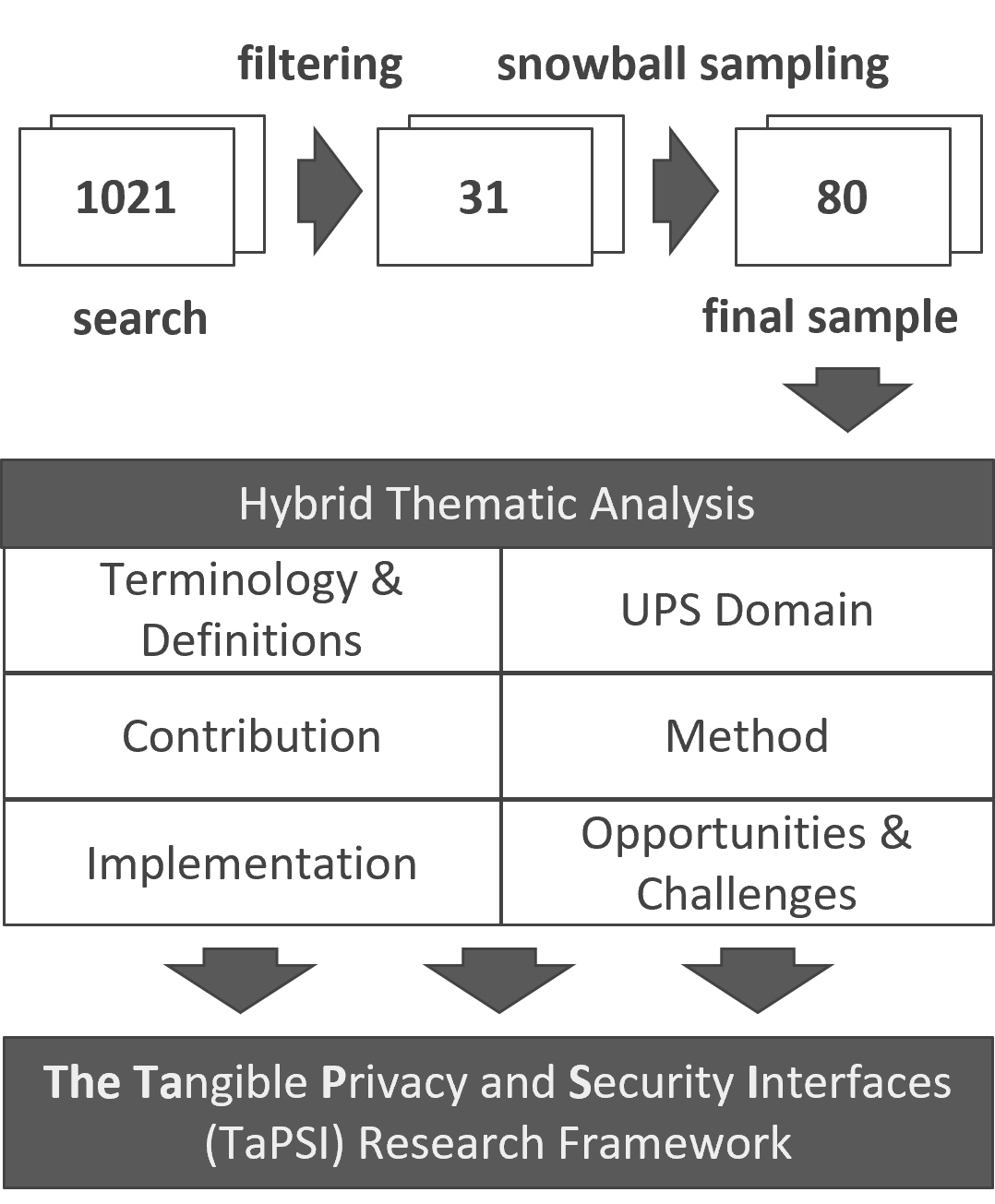
A Systematization of Knowledge on Tangible Privacy and Security Interfaces
We present a comprehensive Systematization of Knowledge on tangible privacy and security interfaces (TaPSI). Tangible interfaces provide physical forms for digital interactions that can offer significant benefits for privacy and security applications by making complex and abstract security concepts more intuitive, comprehensible, and engaging. Through a literature survey, we collected and analyzed 80 publications. We identified terminology used in these publications, addressed usable privacy and security domains, contributions, applied methods, implementation details, and opportunities or challenges inherent to TaPSI. Based on our findings, we define TaPSI and propose the TaPSI Research Framework, which guides future research by offering insights into when and how to conduct research on privacy and security involving TaPSI as well as a design space of TaPSI.
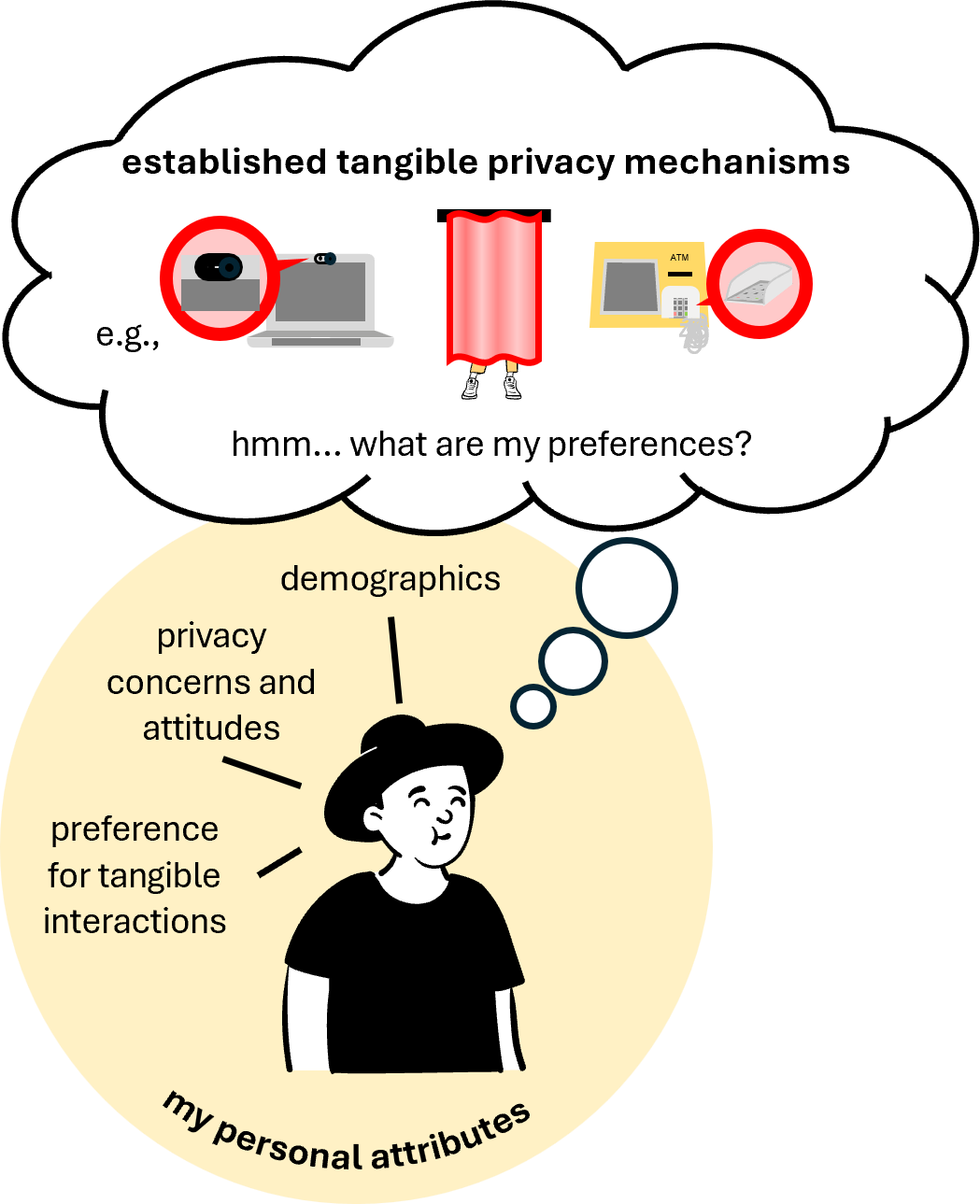
Correlations Between Personal Attributes and Preferences for Tangible Privacy
We explored how personal attributes, such as age, gender, technological expertise, or “need for touch”, correlate with people’s preferences for properties of tangible privacy protection mechanisms, for example, physically covering a camera. For this, we conducted an online survey (N=444) where we captured participants’ preferences of eight established tangible privacy mechanisms well-known in daily life, their perceptions of effective privacy protection, and personal attributes. We found that the attributes that correlated most strongly with participants’ perceptions of the established tangible privacy mechanisms were their “need for touch” and previous experiences with the mechanisms. We use our findings to identify desirable characteristics of tangible mechanisms to better inform future tangible, digital, and mixed privacy protections. We also show which individuals benefit most from tangibles, ultimately motivating a more individual and effective approach to privacy protection in the future.
Act2Auth – A Novel Authentication Concept based on Embedded Tangible Interaction at Desks
Authentication (e.g., entering a password) is frequently perceived as an annoying obstacle when interacting with computational devices, but still essential to protect sensitive data from unauthorized access. We present Act2Auth, a novel concept for embedding authentication into users’ established routines by sensing tangible interactions at desks. With Act2Auth, users can authenticate by performing (secret) routines, such as putting a cup on their desk, rearranging their keyboard, and touching their mouse. The Act2Auth concept is informed by (1) an object analysis of 107 desk photos from Reddit, (2) an online survey (N=65) investigating users’ strategies for creating touch-based authentication secrets, and (3) a technical exploration of capacitive touch-sensing at desks. We then (4) implemented a prototype and evaluated the usability as well as the memorability of Act2Auth compared to textual passwords (N=8). With Act2Auth, we provide fundamental work on how to embed authentication tasks into our daily tangible interactions.

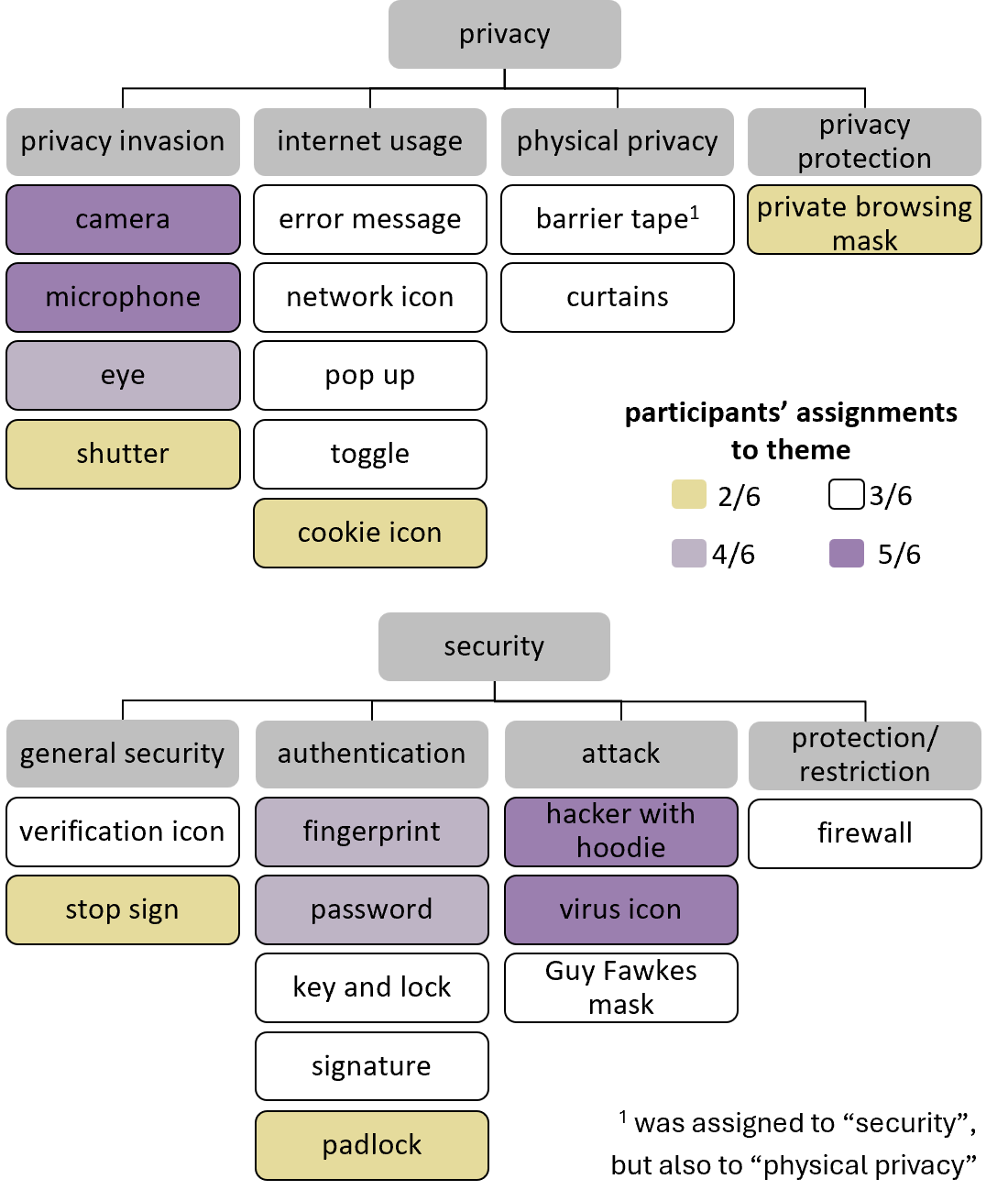
Exploring Symbols and Metaphors for Privacy and Security
The use of symbols and metaphors can be a fast and effective way of conveying abstract concepts. At the same time, misconceived symbols can lead to misunderstandings and errors. Therefore, when it comes to privacy and security, clear communication is essential to avoid putting users’ personal data at risk. In this paper, we elicit 32 symbols and metaphors associated with privacy and security through two brainstorming sessions (n = 8, each). Six experts further separated this collection into security and privacy-related symbols and generated clusters based on similarity. Using participants’ clusters, we derived underlying themes. As a result, we present a symbol and metaphor space for privacy and security and discuss their perceived meaning. Our findings can serve researchers, designers, and developers to find suitable symbols or metaphors for a given scenario (e.g., to decide on the interaction metaphor for a tangible security mechanism) and to understand if a symbol is ambiguous or how it may be understood (e.g., is an eye associated with privacy configurations?). Our work provides an initial knowledge base supporting effective communication in this field.
PriKey – Investigating Tangible Privacy Control for Smart Home Inhabitants and Visitors
The increasing number of smart devices installed in our homes poses privacy risks for inhabitants and visitors. However, individuals face difficulties counteracting privacy intrusions due to missing controls, incorrect mental models, and limitations in their level of expertise. We present PriKey, a concept for device-independent and easy-to-use tangible smart home privacy mechanisms. PriKey is the key to privacy protection: it supports users in taking control over their privacy through meaningful, tangible interactions. Using a Wizard-of-Oz prototype, we explored users’ perceptions regardingPriKey (𝑁 = 16). We then compared PriKey to an equivalent smartphone app (𝑁 = 32), focusing on visitors. Participants perceived PriKey as engaging, intuitive, and benevolent. Their privacy considerations were based on personal and contextual factors. While most participants preferred the smartphone app, others clearly favored PriKey. Our results indicate that tangible privacy is a noteworthy approach for future smart home privacy mechanisms.

